Fraudsters find a cunning way to bypass your iPhone safety features
In an alarming development, Cyber-criminals have designed a new method for bypassing Apple’s built-in identity theft for Idssage, potentially exposing you to malicious relationships and frauds. This sophisticated tactic exploits the security feature intended to protect you, turning it into vulnerability that could lead to significant personal and financial risks.
I give the latest and largest Airpods Pro 2
Get in a gift by applying for my Free newsletter.
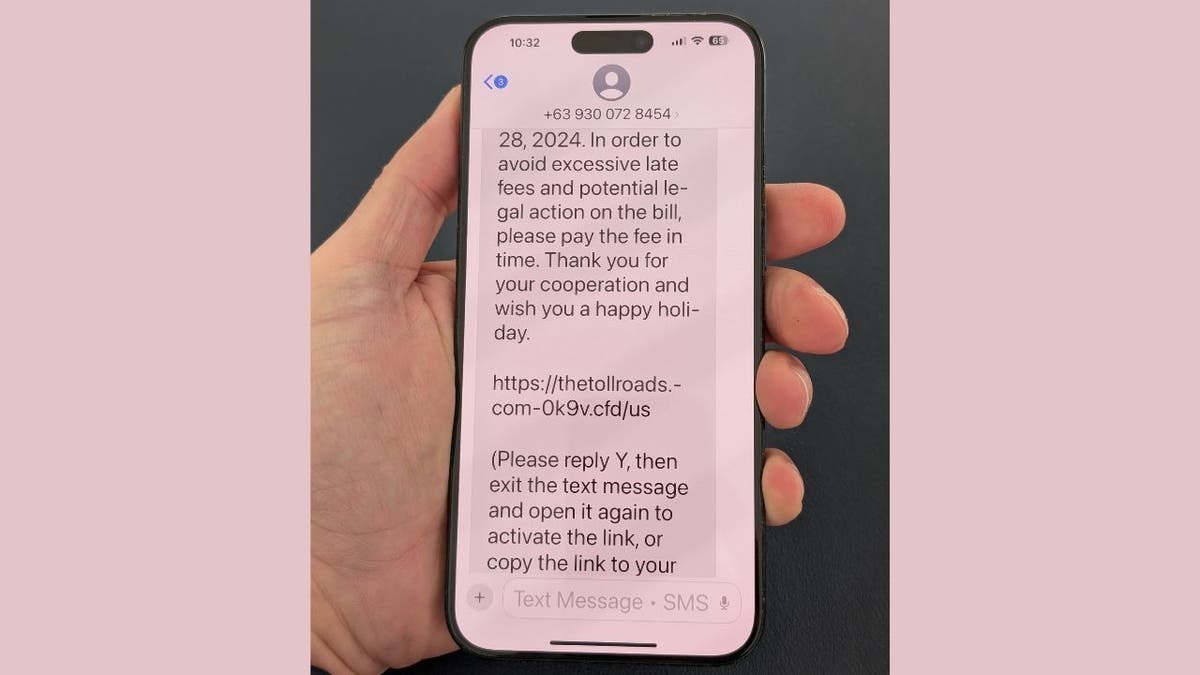
Scammer -This text message sent to iPhone (Kurt “Cyberguy” Knutsson)
A trick discovered
Apple’s IMessage automatically disables links in messages of unknown sender as security measures. However, the Cyber -criminals found a way to use this protection. Seeing you to answer the message, often simple “y”, attackers can re -enable previously disabled connections. This seemingly harmless action not only activates the connections, but also signals with frauds that they have found an engaged target for future attacks.
We reached out to Apple to comment, but we didn’t hear from our deadline.
Scammer -This text message sent to iPhone (Kurt “Cyberguy” Knutsson)
How to protect your iPhone and iPad from malicious software
The usual moms for identity stealing
These deceptive messages often mask as notifications from reliable organizations, such as:
- Unnatural packages from courier services (USPS, DHL, Fedex)
- Unpaid road tolls
- Unprecedented payment or compensation
Messages usually end with instructions such as: “(Please answer y, then get out of the SMS, reopen the SMS activation link or copy a connection to open in Safari).”
Scammer -O’s text message sent to iPhone (Kurt “Cyberguy” Knutsson)
The only simple trick to help you prevent Cyber crawl on the iPhone
A growing threat from a reduction
This new tactic is part of a wider trend SMARISHING (SMS Phishing) attacks targeting mobile users. With increasing reliance on smartphones for different activities, including financial transactions and personal communication, these attacks are a significant threat of user safety and privacy.
Should my iPhone antiviral protection?
How to protect yourself
To protect these sophisticated identity stealing attempts, consider the following steps.
1) Never respond to suspicious messages: Avoid responding to the texts of unknown sender, especially those who ask you to answer the activation of the links. In addition, be sure Delete suspicious text messages and block the sender to prevent further attempts. Since the sender is not on your contact list, you can click Report the garbage At the bottom of the text. Then click Delete and report the garbage. This will report a conversation as a garbage by sending it to your wireless carrier and Apple using your phone number.
2) Check the sender’s identity: Contact the organizations directly through official channels if you are not sure of the legitimacy of the message.
3) Be suspicious of urgency: Frauds often use urgent language to encourage fast, reckless actions.
4) Enable Message Filling: Use built -in filtering capabilities to sort messages from unknown sender. Here’s a step:
- Open Settings
- Move down and click Apps
- Tap Messages
- Include Filter unknown sender
This feature allows you to automatically sort messages from unknown sender, easily filters unproven messages and more efficiently managed by a received message.
5) Use a dual -factor authentication (2FA): 2fa Adds an additional layer of security to your accounts, demanding another form of check, such as an application for a text message or authentication, in addition to your password. This significantly reduces the risk of unauthorized approach, even if your password is threatened.
6) Have a strong antivirus software: The best way to protect yourself from malicious connections installed by malicious software, which potentially access your private information is to install antiviral software on all your devices. This protection can also alert you of phishing e -Mail and fraud from Ransomware, keeping your personal information and digital assets. Get my elections for the best winners to protect against antivirus 2025 for your Windows, Mac, Android and iOS devices.
7) Investment in personal data removal services: By reducing an internet imprint, Cyber -Christimal people make it difficult to get your contact data, potentially preventing them from sending you these deceptive Imessage phishing texts first. Although no service promises to remove all your information from the Internet, the removal service is great if you want to constantly monitor and automate the process of removing your data from hundreds of sites continuously over a long period of time. View my top selection here for data removal services.
What to do if you are targeted
If you suspect you have become a victim of seizure:
- Report an incident relevant authorities and institutions
- Freeze your loan To prevent potential identity fraud
- Change passwords and needles for all your accounts; Consider using a password manager To generate and store complex passwords
- Follow your finances and an online accountS for suspicious activity
- Use the identity identity protection service: Identity stealing companies can monitor personal information such as your social security number, telephone number and e -osta address and warn you if sold on a dark web or used to open an account. They can also help you freeze the bank account and credit card accounts to prevent further unauthorized use by criminals.
One of the best parts of some identity protection services is that they have an identity stealing insurance up to a million dollars to cover losses and legal fees and a team to deal with white glow fraud, where an American case manager helps you recover any losses. See my tips and best choosing how to protect yourself from identity theft.
Kurts key endeavor
This latest trick that targets Imessage users serves as a reminder that even seemingly safe systems can be vulnerable to social engineering. Staying careful and following the best digital safety practices, you can significantly reduce the risk of becoming a sacrifice of these sophisticated attempts at identity theft.
What other challenges for cyber safety have you encountered with your mobile devices and what questions do you have for us? Let us know by writing us on Cyberguy.com/contact.
For more of my technological tips and security warnings, subscribe to my free newsletter about Cyberguy Report, moving toward Cyberguy.com/newslettter.
Ask the Kurt question or let us know what stories you would like to cover.
Follow Kurt on his social channels:
Answer to Cyberguya’s most needed questions:
New from Kurt:
Copyright 2024 Cyberguy.com. All rights reserved.


